Cybersecurity
Security Audit Lab

The purpose of this lab is to gain a familiarity with the internal security audit process of a hypothetical organization. Audits are useful to assess the security of an organization’s security controls and environment, information handling processes, and user practices. They are also useful to determine compliance with regulations.
The following scenario is based on a fictional company:
Botium Toys is a small U.S. business that develops and sells toys. The business has a single physical location. However, its online presence has grown, attracting customers in the U.S. and abroad. Their information technology (IT) department is under increasing pressure to support their online market worldwide.
The manager of the IT department has decided that an internal IT audit needs to be conducted. She expresses concerns about not having a solidified plan of action to ensure business continuity and compliance, as the business grows. She believes an internal audit can help better secure the company’s infrastructure and help them identify and mitigate potential risks, threats, or vulnerabilities to critical assets. The manager is also interested in ensuring that they comply with regulations related to accepting online payments and conducting business in the European Union (E.U.).
The IT manager starts by implementing the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF), establishing an audit scope and goals, and completing a risk assessment. The goal of the audit is to provide an overview of the risks the company might experience due to the current state of their security posture. The IT manager wants to use the audit findings as evidence to obtain approval to expand his department.
My first task is to review the IT manager’s scope, goals, and risk assessment. I will then perform an internal audit to complete a controls assessment and compliance checklist. My IT manager sends me the following email:
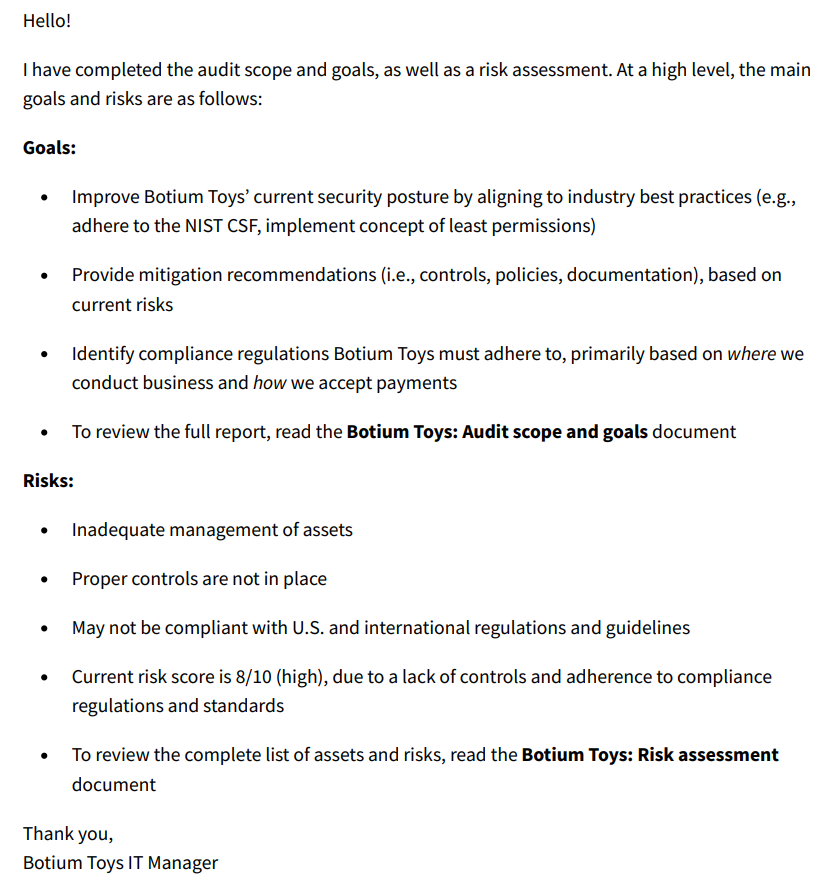
After reading my IT manager’s email, I study the documents that she sent as attachments:
Armed with this knowledge I consider the following questions:
- What are the biggest risks to the organization?
- Which controls are most essential to implement immediately versus in the future?
- Which compliance regulations does Botium Toys need to adhere to in order to ensure the company keeps customer and vendor data safe, avoid fines, etc.?
I then conduct the next step of the security audit by completing a controls assessment to determine which controls should be implemented and why, as well as their implementation priority. While doing this I keep in mind the organization’s current security posture as it relates to the IT department. This includes the following elements:
- On-premise equipment for in-office needs
- Employee equipment: end-user devices (desktops/laptops, smartphones), remote workstations, headsets, cables, keyboards, mice, etc.
- Management of systems, software, and services pertaining to: accounting, telecommunications, databases, security, ecommerce, and inventory management
- All internal network components
- Internet access and reliability
- Vendor access management
- Data center hosting services
- Data retention and storage
- System maintenance, including legacy systems that may require end-of-life maintenance
- Badge readers
What follows is my controls assessment. This document shows the name and type of control, an explanation about what it does, whether it should be implemented or not, and the priority in which it should be implemented. The higher the priority, the more critical the implementation and the sooner it should be done.
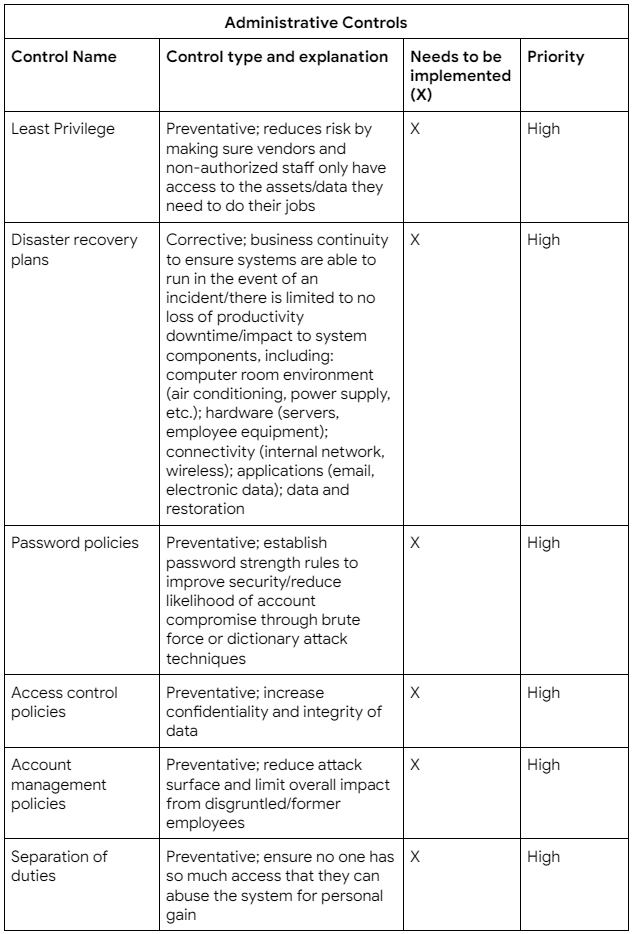
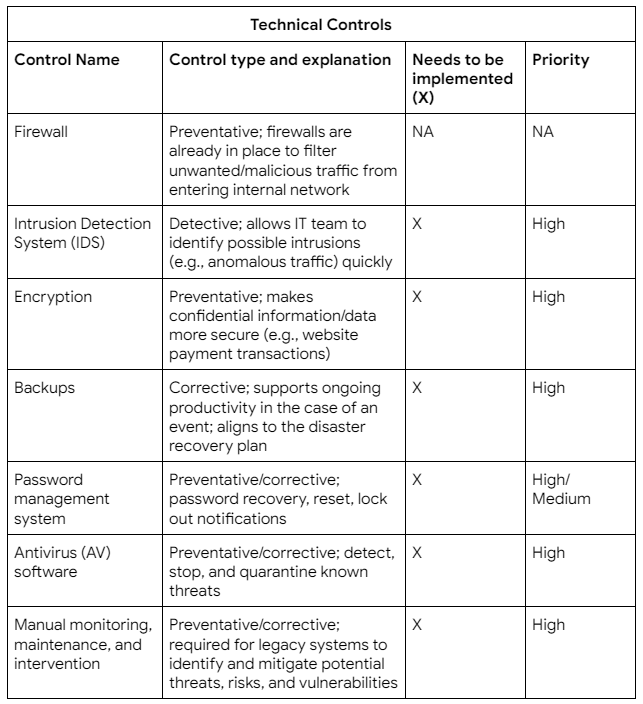
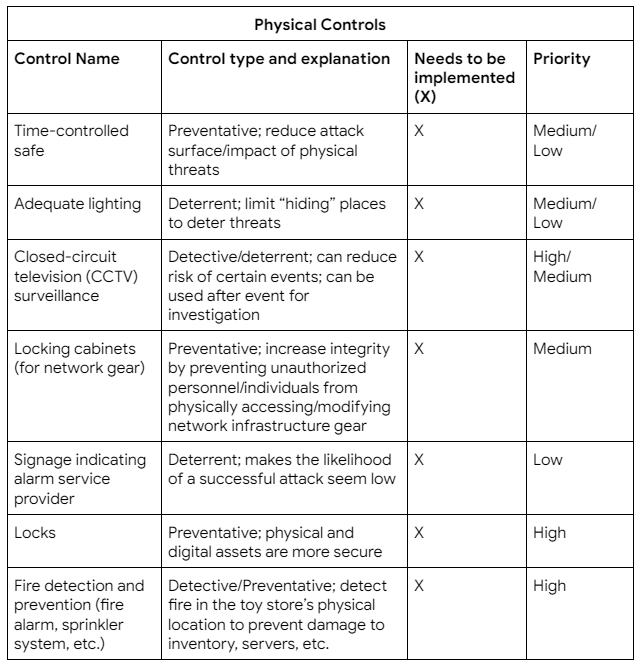
After conducting a controls assessment I also put together a compliance checklist. The purpose of this is to help bring the organization into compliance with regard to regulations, standards, and controls that could impact our business model. I identified the following compliance issues:
General Data Protection Regulation (GDPR)
GDPR is a European Union (EU) general data regulation that protects the processing of EU citizens’ data and their right to privacy in and out of EU territory. Additionally, if a breach occurs and an EU citizen’s data is compromised, they must be informed within 72 hours of the incident.
Botium Toys needs to adhere to GDPR because they conduct business and collect personal information from people worldwide, including those who reside within the EU.
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS is an international security standard meant to ensure that organizations storing, accepting processing, and transmitting credit card information do so in a secure environment.
Botium Toys needs to adhere to PCI DSS because they store, accept, process, and transmit credit card information in person and online.
System and Organizations Controls (SOC type 1, SOC type 2)
The SOC1 and SOC2 are a series of reports that focus on an organization’s user access policies at different organizational levels. They are used to asses an organization’s financial compliance and levels of risk. They also cover confidentiality, privacy, integrity, availability, security, and overall data safety. Control failures in these areas can lead to fraud.
Botium Toys needs to establish and enforce appropriate user access for internal and external (third-party vendor) personnel to mitigate risk and ensure data safety.
Finally, the IT manager has asked me to put together a stakeholder memorandum that summarizes my findings and recommendations. She wants to be able to present this information to higher ups in a way that is clear, concise, and impactful. I drafted the following:
TO: IT Manager, stakeholders
FROM: Chase Anderson
DATE: 06/01/2023
SUBJECT: Internal IT audit findings and recommendations
Dear Colleagues,
Please review the following information regarding the Botium Toys internal audit scope, goals, critical findings, summary and recommendations.
Scope:
- The following systems are in scope: accounting, end point detection, firewalls, intrusion detection system, SIEM tool. The systems will be evaluated for:
- Current user permissions
- Current implemented controls
- Current procedures and protocols
- Ensure current user permissions, controls, procedures, and protocols in place align with PCI DSS and GDPR compliance requirements.
- Ensure current technology is accounted for both hardware and system access.
Goals:
- Adhere to the NIST CSF.
- Establish a better process for their systems to ensure they are compliant.
- Fortify system controls.
- Adapt to the concept of least permissions when it comes to user credential management.
- Establish their policies and procedures, which includes their playbooks.
- Ensure they are meeting compliance requirements.
Critical findings (must be addressed immediately):
- Multiple controls need to be developed and implemented to meet the audit goals, including:
- Control of Least Privilege and Separation of Duties
- Disaster recovery plans
- Password, access control, and account management policies, including the implementation of a password management system
- Encryption (for secure website transactions)
- IDS
- Backups
- AV software
- CCTV
- Locks
- Manual monitoring, maintenance, and intervention for legacy systems
- Fire detection and prevention systems
- Policies need to be developed and implemented to meet PCI DSS and GDPR compliance requirements.
- Policies need to be developed and implemented to align to SOC1 and SOC2 guidance related to user access policies and overall data safety.
Findings (should be addressed, but no immediate need):
- The following controls should be implemented when possible:
- Time-controlled safe
- Adequate lighting
- Locking cabinets
- Signage indicating alarm service provider
Summary/Recommendations: It is recommended that critical findings relating to compliance with PCI DSS and GDPR be addressed promptly because Botium Toys accepts online payments from customers worldwide, including the EU. Additionally, since one of the goals of the audit is to adapt to the concept of least permissions, SOC1 and SOC2 guidance related to user access policies and overall data safety should be used to develop appropriate policies and procedures.
Having disaster recovery plans and backups is also critical because they support business continuity in the event of an incident.
Integrating an IDS and AV software into the current systems will support our ability to identify and mitigate potential risks, and could help with intrusion detection, since existing legacy systems require manual monitoring and intervention.
To further secure assets housed at Botium Toys’ single physical location, locks and CCTV should be used to secure physical assets (including equipment) and to monitor and investigate potential threats. A fire detection and prevention system needs to be installed as well in order to protect personnel, inventory, and the physical network.
While not necessary immediately, having a time-controlled safe, adequate lighting, locking cabinets, and signage indicating alarm service provider will further improve Botium Toys’ security posture.
Final thoughts:
I completed this lab during my Google Cybersecurity Professional Certificate course. I found it interesting and thought provoking because it exposed me to basic yet essential tasks within the realm of governance, risk, and compliance (GRC). I was asked to analyze everything from pertinent regulatory compliance measures to internal controls that would help reduce the operational risk of a fictional toy company. It also helped me practice communicating security ideas with pertinent stakeholders, an important skill set to be sure.